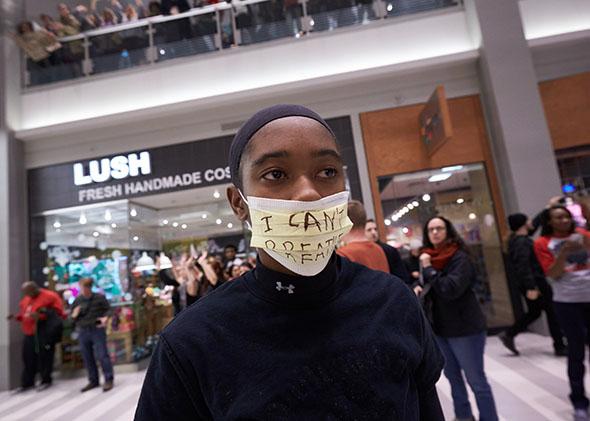On Dec. 20, a Black Lives Matter protest drew as many as 3,000 people to the Mall of America rotunda. Twenty-five protesters were arrested, and the city of Bloomington, Minnesota, also filed charges against 11 alleged organizers for offenses such as unlawful assembly, trespassing, disorderly conduct, and public nuisance. The city of Bloomington is still seeking $25,000 in restitution (to cover police overtime) from the 11 people charged.
Now comes a new chapter in the story. Software engineer Tony Webster did not attend the demonstration, but he filed a public records request on Dec. 23 under the Minnesota Government Data Practices Act for data related to it, including emails, files, voicemails, call logs, police radio communications, trespass notices, and other information. The city of Bloomington did provide him some access to a small amount of the requested information but not enough for Webster. On June 19, he filed a lawsuit against Bloomington. The complaint states that the city withheld, concealed, and likely destroyed data in violation of Minnesota’s Government Data Practices Act.
His suit highlights an increasingly frustrating situation with government data use. Local and federal government agencies are incredibly high-tech when it comes to surveillance capabilities, eagerly investing in modern-day spy equipment. But when it comes to very basic tools to handle public records requests, these same agencies are stuck in the ’70s.
Among other things, the complaint alleges that Bloomington denied Webster access to a large amount of the data he’d requested and eventually refused access to it altogether, claiming that his requests were meant to harass the city in retaliation for its decision to prosecute Black Lives Matter protesters. (In the interest of full disclosure: Webster and I were on the same team at the Nerdery Overnight Website Challenge, an annual 24-hour volunteer event, in April 2014. But we are not close.)
According to Webster, the city responded to his initial request by providing him access to a small portion of data—he estimates about 750 out of the 58,000 emails located that were related to his request. Webster wasn’t granted permission to download files on his own USB drive and instead had to use a city computer that he says had significant software limitations. (During one session, he says, the city assigned a uniformed police officer to observe him while he inspected the data.) He was told he could access some files in hard copy or PDF, which meant that he couldn’t open video and audio attachments—and he couldn’t examine their contents or metadata. Metadata, as you may recall from the early days of the Edward Snowden leaks, includes information on when and where a document was created and modified, for example, as well as who created it. A photograph’s metadata might include the location of an image, the type of camera used to capture it, and the time and date the photograph was taken. Webster wasn’t sure what he might find by inspecting metadata, but he thought it would provide a more complete picture of the city’s actions surrounding the protest. Yet he was allowed to look at only a tiny amount of relevant metadata.
In a letter to Webster, Bloomington city attorney Sandra Johnson said that the city did not have to release all of the metadata because it was not classified as a public record. To make that case, she misleadingly cited an appellate decision from an Arizona court and said that “metadata ‘mining’ can often result in inadvertent disclosure of privileged material.” But that case had already been overturned by the time Johnson wrote the letter. (Amy Schmidt, acting city attorney while Johnson was out of the office, declined to comment.) The Arizona Supreme Court, Washington Supreme Court, and appellate courts in both Illinois and New York have all upheld that metadata for electronic public records must be produced in response to public records requests.
Privacy advocates have long argued that private citizens’ metadata, which is generally accessible to the government without a warrant under the “third party doctrine,” is incredibly revealing. For instance, Instagram location metadata uncovered by Associated Press was used to expose disgraced Rep. Aaron Schock for spending “taxpayer and campaign funds on flights aboard private planes owned by some of his key donors.”
Even the small amount of metadata that Webster was allowed access to proved illuminating. For instance, he used it to discover that the Mall of America had created a fake Facebook account to friend and monitor protesters. He also says that he was further able to determine that the city had withheld, altered, or destroyed requested data, a key portion of the lawsuit he filed. His complaint alleges that some files had changed size between when he inspected the documents Feb. 20 and when he returned to look at them March 6 and that a sequentially numbered photograph was found in the external hard drive’s recycle bin.
Cleary, public records requests can lead to the uncovering of government misconduct. If, in fact, any data—including metadata—needs to be withheld because it is deemed confidential or privileged or exempt under state or federal law, the city of Bloomington could simply redact or deny access to that specific data rather than denying access altogether.
“The exemptions built into open government requests are really meant to take into account harm that could result from information being revealed. You can’t create a new exemption by simply saying that harm will result. You have to say that this is the identified harm and this is why it’s been recognized—that calculus has been done already,” said Amie Stepanovich, U.S. policy manager at Access, a nonprofit organization defending digital rights.
Within government, data collection is often done in a haphazard way, according to Michael Morisy, journalism fellow at Stanford University and founder of Muckrock, a news tool that helps file, track, and share public records requests. Morisy says that in many cases, public records officers simply email a few people and ask them to search their inboxes for relevant emails and files. That approach may be quicker than tracking down a part-time information technology person, for example, but it can lead to an astounding amount of data getting overlooked, intentionally or otherwise.
Earlier this month, the House Committee on Government Oversight heard testimony from journalists and members of transparency organizations about the significant barriers faced in response to Freedom of Information Act requests, including delays, redactions, and even retaliation. It is easy to assume bad faith on the part of government agencies. However, it’s possible that some are simply poorly equipped to handle even the most simple of requests.
It’s long past time for agencies to invest in training and tools that will enable them to properly review and redact emails and files and release them to the public. Government resources should be spent on ways to enable greater transparency and accountability, not just surveillance of citizens.
This article is part of Future Tense, a collaboration among Arizona State University, New America, and Slate. Future Tense explores the ways emerging technologies affect society, policy, and culture. To read more, visit the Future Tense blog and the Future Tense home page. You can also follow us on Twitter.