Just two and a half months ago, 22-year-old Marcus Hutchins, a British security researcher, was hailed as an international hero for putting a stop to the WannaCry ransomware attack. But on Thursday, as he was arrested on charges that he was behind a banking hack in 2014 called the “Kronos banking trojan,” according to a federal indictment against him.
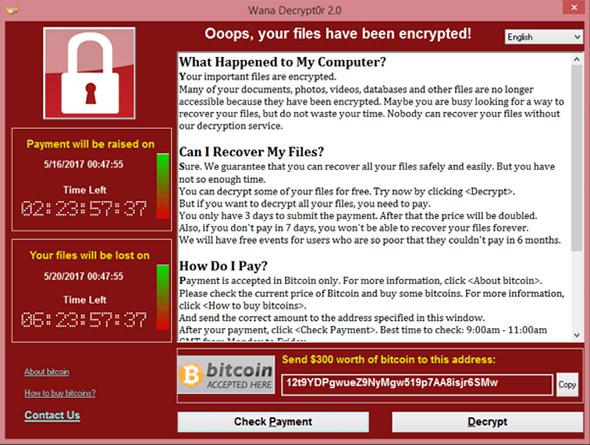
Hutchins was the subject of international praise after he discovered the kill switch that shut down WannaCry, which had infected hundreds of thousands of computers in 150 countries around the world, including hospitals throughout the U.K., as well as utility systems in Spain and parts of the Russian government. Once infected, computers were locked and their files encrypted until victims paid about $300 in bitcoin to regain access. Hutchins, who works for the Kryptos Logic security firm, examined WannaCry’s code and found a domain name that, when registered, prevented the malware from spreading any further.
Hutchins was arrested in Las Vegas after he attended the annual hacker convention DefCon, as Motherboard first reported. The indictment includes a second defendant, but that name has been redacted.
Kronos, the malware program that Hutchins is accused of helping unleash, stole internet banking credentials and credit card data by sending emails with compromised attachments, like infected Microsoft Word documents, that were used to spread the attack, according to the Guardian. An ad for Kronos on Russian forums in 2014 priced the malware package at $7,000.
On Wednesday night, Quartz reported that the bitcoin accounts where victims of WannaCry were asked to deposit their ransom had been completely emptied. However, that could be a coincidence—there’s as yet no clear link between the emptying of the bitcoin accounts and Hutchins.
Whatever happens to Hutchins, there’s one sure lesson from all the exploits that he’s been associated with: Use caution when opening email. Even if it looks like it’s from someone you know, check the actual email address, and if you’re at all unsure, don’t open any attachments or click on links. Anyone able to exercise that level of personal restraint would be doing better than the people who work at the highest level of the United States government. On Monday night it was revealed that numerous members of the Trump administration had exchanged emails with a prankster pretending to be White House staffers and even Trump family members. Even the White House homeland security adviser, Thomas Bossert, who is supposed to be a cybersecurity expert, was duped.