Ransomware is just as sinister as it sounds. It’s malicious software that holds data hostage for, yup, a ransom. Ransomware attacks are prevalent on computers running Windows, but so far Apple’s OS X operating system for Macs has been mostly spared. Those days seem to be numbered, though.
On Sunday, security firm Palo Alto Networks detailed the discovery of Mac ransomware called KeRanger in an update of the BitTorrent client Transmission. The firm first found the malware on Friday, and Transmission customers started noticing it Saturday.
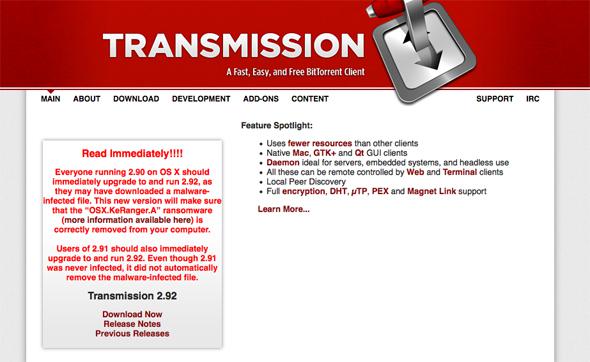
Hackers compromised Transmission’s website and injected an adulterated version of the 2.90 software update for users to download. The KeRanger ransomware was designed to lurk for three days and then begin encrypting certain personal files. The ransom to have them decrypted is one bitcoin (currently about $412).
Transmission isn’t sold through the official Mac App Store, but KeRanger was signed with a legitimate Mac app development certificate, so it breezed right past OS X’s Gatekeeper protection.
Transmission quickly posted a clean version of its update, called 2.91, and then an additional version 2.92, which also removes the malware. When Palo Alto Networks raised the alarm on Friday, Apple quickly revoked the certificate KeRanger was using to avoid suspicion and updated its XProtect antivirus system.
Though hackers don’t usually target Apple devices, there have been some examples of ransomware attacks on Macs before. Still, Palo Alto Networks threat intelligence director Ryan Olson told Reuters that KeRanger is significant because it is “the first one in the wild that is definitely functional, encrypts your files and seeks a ransom.”
Macs have largely avoided scrutiny and attack because Windows PCs have dominant market share. This has created a feedback loop in which most black-hat hackers who profit from malware have more experience developing their malicious software for Windows. David Kennedy, the founder and CEO of cybersecurity firm TrustedSec, points out, though, that if the Windows market becomes saturated enough with ransomware attacks, bad actors may turn to Macs in search of new victims. Even without the huge enterprise presence that Windows PCs have, hackers could still make money from targeting individual consumers who own Macs (as in this situation with Transmission).
Apple is generally proactive and swift about addressing attacks like KeRanger. The company will release patches or make changes within days, instead of waiting for a patch release schedule the way Microsoft does. But if Macs were barraged with malware the way Windows machines are, it would be difficult for Apple to maintain this approach.
Kennedy says that the quick responses to individual situations may create disincentives for hackers to go after Apple products in the first place, though. “It probably took a significant amount of time to hack the Transmission site, develop the ransomware, and set up the attack infrastructure. And then it was patched within a day,” he said.
Still, the KeRanger attack indicates that hackers may be leaning toward developing clever Mac malware, in spite of Apple’s defense resources. “It’s definitely a trend that’s going to hit more,” Kennedy said. “Ransomware is an interesting business model. The hackers who develop it don’t care who they impact. It’s just a profit game.”