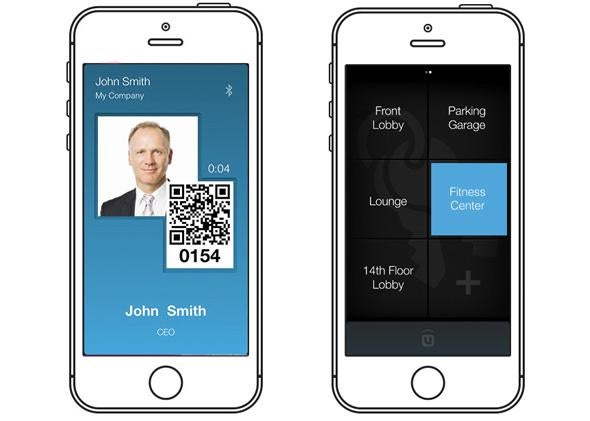
We all participate in the physical security of the places we visit every day. We have the keys to our houses, maybe the keys to our neighbors’ or parents’ homes, fobs for our gyms, and badges for our offices.
Usher is moving forward, though. The servce has already been adopted in numerous large-scale settings, including by defense contractor Northrop Grumman and by Georgetown University as the campus ID card for this year’s entire freshman class. Usher is free for individuals to try and $10 per user per month for up to 10,000 enterprise users.

Graphic from Usher
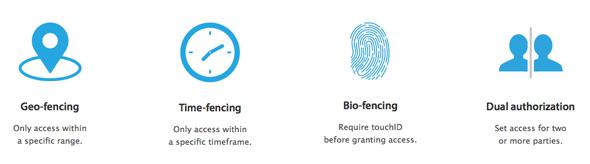
Created by the business software and analytics company MicroStrategy, Usher combines and manages a lot of different types of authentication (making sure you are who you claim to be) with the promise of making businesses secure. It’s like a digital wallet, but for all of that other random junk you carry around. And Usher offers plenty of choice for authentication methods. You don’t have to deploy facial recognition if you want to use fingerprint scans. Or you can scrap all of that and go with QR codes, and then change your mind again and use proximity sensing through geofencing and Bluetooth. The options can also be used in combination.
Graphic from Usher
Usher’s main assumption is that people are deeply bonded with their smartphones. Unlike keys or a fob that you might not realize are missing for hours, Usher assumes that you always know where your mobile devices are, because they’re always on you and in use. Of course, the system also has contingencies for lost or stolen phones, but the central idea is that having all company badges, keys, and software access on one smartphone is what people would want if they could choose any security system.
“We’re solving a massive problem in a really elegant way,” said Jonathan Klein, the president of MicroStrategy. “If you can combine security with data and with mobile, and you’re good at all those things, you can do something that’s really groundbreaking.”
We hear about hacks and breaches all the time, so a one-stop shop for security sounds like just what Target, Sony, and the Post Office need, especially when it’s coming from an experienced enterprise company. MicroStrategy may not have released extensive security products before, but the company has been building enterprise software since 1989. And Klein says that the product has undergone substantial third-party review. “We’ve worked with a number of leading firms … who come in and try to hack into your product, they try to break it, they try to look for security vulnerabilities,” he says.
Some hackers-for-hire have questions about Usher’s security, though. Alex McGeorge, the head of threat intelligence at the security analysis firm Immunity, says that if he were to attempt to hack Usher, he sees some options for where he would start. “There’s some interesting stuff here, but the thing that strikes me is that this is still dependent on the phone, so it depends on the security model of the phone. And phone security isn’t all that great,” he said. “[Usher data] is encrypted between the phone and the server. That’s great, that’s necessary. But if I own your phone and you’re displaying something on the phone then I can take a screenshot of the thing you’re displaying, I can grab your fingerprint scan, or I can grab your PIN by monitoring which buttons you press on the virtual screen. If someone put me up against this thing, I would have a plan of attack.”
As with any service, the tension between security and usability plays out in Usher as well. Offering so much flexibility for consumers in terms of customizing which authentication measures they want to use means Usher has to defend an extensive array of subsystems against attackers. “Without taking the application and reverse-engineering it, I can’t talk about its specific security posture,” said Geoffrey Vaughan, a security consultant at Security Compass. “But what I can tell you is that … when you see these apps that try to do everything, the footprint of them is very large. As an attacker I don’t have to find all the ways into the system, I just have to find one way and I win.”
With high-profile hacks happening all the time, it’s clear that we need big changes in cybersecurity. Whether or not Usher is “lightning in a bottle” like the company thinks it is, trying new approaches is the only way to make progress. “As soon as you put a team together of people whose only mission is to break software, it’s gonna happen. This is inevitable with any piece of software,” McGeorge said. “But that being said, if someone did implement [Usher], it would raise the bar from the attacker perspective of what they would have to do in order to win. And, you know, that’s not bad.”