Printers aren’t exactly hip these days, but they still lurk in our offices and homes. They’ve subtly advanced over the last several years to include extras like Wi-Fi connectivity and nice color screens. Unfortunately, adding new features to uninteresting devices means that security isn’t always on developers’ minds.
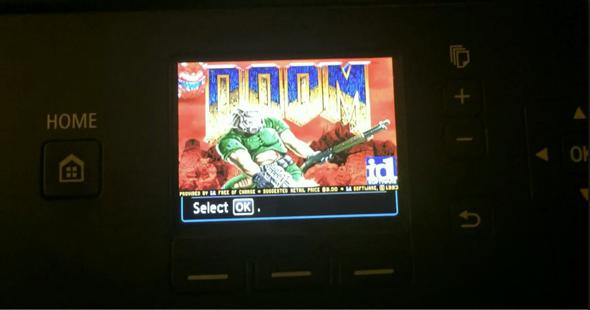
All of this has allowed one cybersecurity researcher to install and play the 1993 classic video game Doom on a Canon Pixma printer. Which is both worrying and awesome.
Michael Jordon, a researcher at Context Information Security, wrote a blog post for Context detailing his hack and “demonstrating current insecurities in devices categorised as the ‘Internet of Things’.” Though it took four months to get Doom up and running, Jordon’s broader goal was to experiment with the vulnerabilities he had found and present them in an interesting way to get people’s attention. Canon says it will fix the vulnerability “as quickly as is feasible.”
The Web interface that Pixma printers use to allow remote status checks of things like ink levels isn’t protected by a password because it doesn’t do much. As Jordon explains out, “you could print out hundreds of test pages and use up all the ink and paper, so what?” But he found that in the process of updating the firmware (the code that coordinates the interaction of hardware and software in a device), he could freely control where the printer checked for the update. This means that a malicious hacker could direct the printer to install an “update” that was really malware. And if the newly infected printer was, say, on an office network, that malware could then be used to infiltrate deeper and into more information-rich devices like servers.
Pixma firmware is encrypted, which is good. But Jordon says he was able to crack the encryption and use that to his advantage, because it allowed him to make his malware look trustworthy to the printer he was installing it on. Jordon reports that there are thousands of vulnerable Pixma printers online right now.
But what about Doom?
He told BBC News, “Running Doom, that’s real proof you control the thing.” The printer he used has convenient specs for Doom, including a 32-bit Arm processor and a screen with the correct aspect ratio. “I had all the bits, but it was a coding problem to get it all running together,” he told the BBC. You can watch a video of the printer running Doom here.
At least something good came out of this bug.