It is designed to secretly infiltrate targeted computers or mobile phones to monitor communications and siphon data. Now, a controversial surveillance Trojan sold to law enforcement and intelligence agencies has been linked to 25 countries across the world—with new research revealing the extent of what it calls “the unchecked global proliferation” of government-grade spy tools.
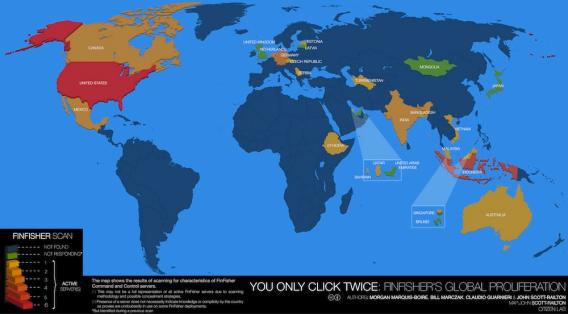
A report published today by security experts at Citizen Lab discloses what it says are the locations of servers used to control sophisticated surveillance technology sold by Gamma Group—and the list of countries implicated is extensive, from Qatar and Mongolia to the United States and Canada.
Gamma’s “FinSpy” can bypass antivirus systems, record Skype chats and emails, log what targets are typing on their keyboards, and even conduct “live surveillance” through a user’s webcam or “silently extract” files from a computer’s hard disk, according to marketing materials published by WikiLeaks. Gamma says it sells the software to authorities to help them monitor “bad guys” like terrorists and organized crime gangs. However, a growing body of evidence suggests the tool has been obtained by repressive governments that have used it to target political opponents and activists.
Citizen Lab, which is based at the University of Toronto’s Munk School of Global Affairs, disclosed today that it has identified 36 active servers in a total of 25 countries used to control deployments of FinSpy. The countries are: Australia, Bahrain, Bangladesh, Brunei, Canada, Czech Republic, Estonia, Ethiopia, Germany, India, Indonesia, Japan, Latvia, Malaysia, Mexico, Mongolia, Netherlands, Qatar, Serbia, Singapore, Turkmenistan, United Arab Emirates, United Kingdom, United States, and Vietnam.
The group says that the discovery of FinSpy servers in a country does not mean it is necessarily being used by that country’s law enforcement or intelligence agencies, because the servers could have been purchased by actors from any country and used as a “proxy” service. Given that the United States has shown up on the list linked to a series of FinSpy servers, I asked the FBI whether it had purchased Gamma’s surveillance technology. Bureau spokesman Christopher Allen said as a matter of policy he could not “confirm specific products or services that the FBI may or may not purchase or use.” The report also noted that one of six U.S. spy servers is registered to Verizon Wireless. Debra Lewis, a spokeswoman for Verizon, told me she was “not aware of this” but would look into it. She had not provided any further comment at the time of publication.
What the findings do conclusively show, the Citizen Lab report says, are “troubling cases of FinSpy in countries with dismal human rights track records, and politically repressive regimes.” In Ethiopia, for instance, the group was able to identify images of an opposition political party called Ginbot 7 designed to be used as “bait” to infect users with the Trojan. The researchers were also able to obtain a sample of FinSpy designed to infiltrate mobile phones intended for use in Vietnam, a country with a record of suppressing all forms of political dissent. This builds on a Citizen Lab report last year that revealed how Gamma’s surveillance technology was used to target Bahraini activists, and follows a wider trend of other Western-made spy tools being used against journalists and dissidents in countries notorious for cracking down pro-democracy activities.
Gamma, which was yesterday dubbed a “corporate enemy” of the Internet in a report by Reporters Without Borders, had not responded to an emailed request for comment at the time of publication. In January, the company’s spokesman Martin Muench told me during a lengthy exchange that Gamma adhered to German, U.K., and U.S. export regulations and “does not discuss its client base, its exports, or any of the operations which its clients may or may not be undertaking.”