This article originally appeared in Business Insider.
The mechanism that lets you use your Twitter account to log in to websites and mobile apps allows those third parties read your private direct messages and send them too, according to Rishi Lakhani, a search marketing consultant. Although the login is designed that way by Twitter—it’s not a flaw, it’s a feature!—most Twitter users have no idea that their private direct messages are readable by apps and websites when they use that login to sign in to other apps and sites.
Lakhani demonstrated the phenom on a Twitter account created by Business Insider. Even though Lakhani did not have the password to the account, Lakhani was able to gain control of it within seconds, alter the profile description on the account, and send and receive direct messages.
Twitter declined to comment.
It is not clear how many users are affected. Twitter has 284 million users, and thousands of other companies let users log in to their sites and apps via Twitter. Business Insider is one of them.
The login appears to be designed deliberately for apps that use Twitter, such as Tweetdeck or Hootesuite, which are dashboards that make it easier to control your Twitter account. Obviously, those apps need to be able to handle DMs when you use and receive them through the app. Users are asked for their permission when they first login.
What Lakhani is saying, however, is that there are sites out there that have no business reading or sending DMs—yet they nonetheless have the power to do so. And while most users will realize that the app needs permission to handle DMs, they don’t realize that developers at the app company itself can now control the account, inclusing sending and reading those DMs.
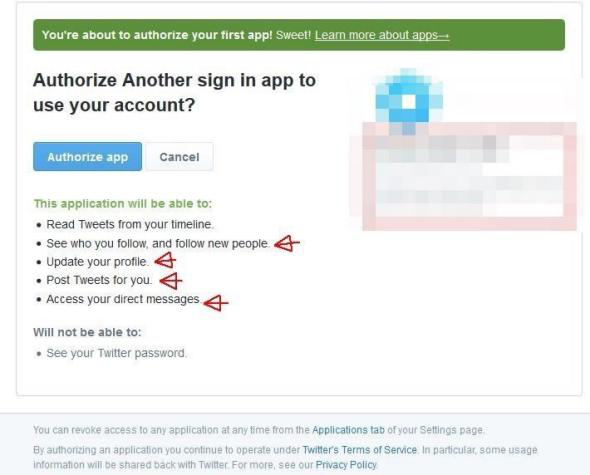
Lakhani discovered the hole when he tried to use his Twitter account to sign up to Inbound, a forum for digital marketers. He discovered that the login disclosure warned him that the site would be able to read his DMs. Inbound apparently did not realise it had that power over Twitter users on the site. Inbound was doing the same thing that thousands of other companies do: Letting people use their Twitter accounts to login to the site in order to make the registration process go more quickly.
After poking around, Lakhani realised that the API (application programming interface) that Twitter was letting developers use as a login tool let those developers choose one of three options:
- Read Only
- Read Write
- Read Write DM
In other words, a developer who wants to stick one of those login boxes on their site could choose the third option and it would mean that any user who logs in is exposing their direct messages to the site or app. This is what the login choice menu looks like:
Rishi Lakhani
Needless to say, the login access is open to abuse, Lakhani says, writing on the Refugeeks website:
A clever spammer could use this tool to their advantage, as it allows some real control over an account’s actions. For example, by time noting user activity, it could be possible to use the account to tweet links for traffic etc when the user is least likely to be using the account, and then delete them. the same goes for DMs.
See Also: Apple’s iTunes Is Now on Tumblr
