Fighting the war on drugs is like peeling an onion: Every layer removed only reveals another. Waging that battle on the secured, encrypted Tor network—which itself stands for “the onion router”—poses its own challenges.
The trial of alleged Silk Road mastermind Ross Ulbricht, who’s been charged with drug trafficking and money laundering, is about to conclude, but it’s only a layer in the federal government’s efforts to stem crime online. The Tor-hosted black market for drugs and other contraband was once one of the Dark Web’s biggest sites, yet operated in near-total anonymity. But no matter how the trial ends, it won’t stop online trafficking. After the FBI shut down Silk Road and arrested Ulbricht in October 2013, it took only a month for a successor, Silk Road 2.0, to open. It, too, eventually got shut down by the FBI, and now other online black markets have replaced it.
That’s why the Silk Road trial is less about stopping illegal activity than about setting the guidelines for future investigations, stings, and prosecutions in what is starting to look like a never-ending game of cybercrime Whac-A-Mole. In that sense, Ulbricht’s trial is a volley in a much broader trial against privacy and anonymity.
One indicator is the case against Ulbricht. Via an accidental leak, the Daily Dot obtained the entirety of the government’s evidence. For all the high-tech shimmer of the case, it’s pretty prosaic: Ulbricht’s many fake IDs, his emails, chats, an incredibly damning journal, and screenshots of Ulbricht’s $6.7 million Bitcoin account page hosted on the Silk Road’s website under “/mastermind” (yes, really). This is not high-tech surveillance evidence; this is stuff they pulled off his laptop after inserting a Homeland Security mole into his moderation staff.
Still, things do not look good for Ulbricht. My Slate colleague Justin Peters explained how both Ulbricht and alleged Silk Road 2.0 operator Blake Benthall were done in by a combination of sloppiness, greed, and hyperlibertarian idealism. But their successors could be smarter. How are we going to deal with them? The issue ultimately gets at the root of our right to be private online—or the lack thereof. While the prosecution is rolling over Ulbricht—whose defense has made a somewhat stretched attempt to show that the real mastermind was the former head of Bitcoin exchange Mt. Gox, Mark Karpeles—the real significance of the trial is its role in the government’s war on anonymity and privacy. Ulbricht, who could face 30 years in prison or more if convicted, is certainly on trial, but so is Tor.
The Internet was not designed for privacy—far from it. For communication over the open Web, you reach a site by typing in its domain name system, or DNS, address, like www.slate.com, which your computer then looks up in a DNS server to find the actual IP address (Slate’s is currently 184.29.104.192). Think of the DNS address as a person’s name and the IP address as her street address. Except in this system, you can find anyone’s address just by knowing her name.
Consequently, absolutely nothing about this lookup system is private. Internet communications work very much like the mail system: You address a message (or packet) to its final destination, and the message is taken by multiple carriers through a series of hops to that destination. Every carrier sees both the sender and the destination. DNS acts as the telephone book, the fundamental directory of the Internet. The centralized control of DNS allows effective control over what sites are permitted, which is why pirate sites like the Pirate Bay periodically have to hop countries (from thepiratebay.ac to thepiratebay.se, for example) as one government or another cracks down on them.
But for drug trafficking and the like, DNS is no good, since the DNS record points right to your server’s physical location. For anonymity, what is needed is a way to bypass DNS altogether, and that brings us to Tor, originally developed by the U.S. Naval Research Laboratory. Tor is a distributed network that routes communications through everyone online using its software, without any central nexus. Through a lot of technical cleverness, Tor uses cryptography so that in delivering a message, each relay knows the address of only the next step, not the final destination or the sender—that is, each sees only one layer of the onion. That fixes the IP privacy problem. Tor also offers a “Hidden Service Protocol” that allows for registering servers under the .onion pseudo-domain. That gets around DNS, so Tor users (and only Tor users) could reach the Silk Road at the address http://silkroadvb5piz3r.onion, and the government can’t do anything to shut it down without both locating and seizing the server at that address—which Tor deliberately makes very difficult to do. (Going to that address now tells you that the FBI has seized the site, so don’t get your hopes up.)
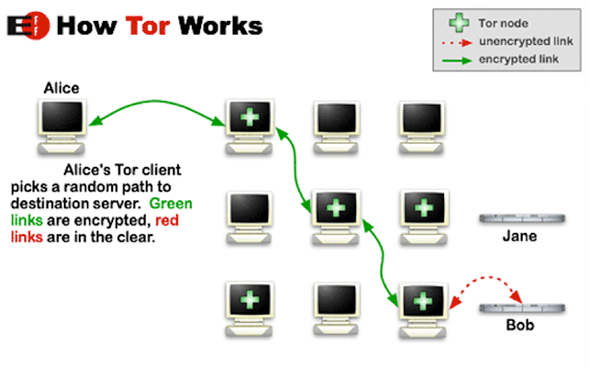
Courtesy Electronic Frontier Foundation
Law enforcement, needless to say, is not a big fan of Tor, and the Silk Road trial is only one facet of a general push to restrict encryption and privacy. Barack Obama, David Cameron, and FBI Director James Comey are all calling for government-accessible backdoors into technology. As Andy Greenberg explains, the Department of Justice’s fear-mongering claim that 80 percent of Tor traffic is child pornography is false—it’s more like 1 percent, which is obviously much worse than zero percent, but not quite the pandemic the government suggests.
But cracking down and restricting the use of Tor and other anonymizing services won’t help. Technology without backdoors will always be available to criminals, so the only people who will sacrifice privacy will be law-abiding citizens. The only benefit to be gained from restricting privacy in this way is to make it more likely that a random person using anonymizing services is a criminal, turning the use of encryption into probable cause. This is, in fact, how Harvard caught Eldo Kim, a student who made a fake bomb threat to get out of an exam. Since he was one of the very few people using Tor on the Harvard wireless network at the time the threat was sent, the FBI quickly identified him even though it was unable to see the contents of what he was doing. But that doesn’t mean that use of Tor should be tantamount to probable cause in and of itself, nor that the use of such services should be compromised.
Rather than restricting technology, the best law enforcement approach seems to be the old-fashioned one: police work. The Silk Road 2.0 was infiltrated from the very beginning by FBI agents, who monitored discussion boards and tracked suspects, easily identifying administrator Benthall, aka “Defcon.” (The proliferation of black markets—tech journalist Joseph Cox listed “Agora, Evolution, Blackbank, Nucleus, Outlaw” as just a few—may force us to question the Whac-A-Mole approach on a legislative and policy level. Ulbricht’s laptop was obtained in an unencrypted state because FBI agents made sure he was using it when they arrested him, before he had a chance to lock it down.
Tor and other anonymizing tools have very beneficial uses, from simple protection from the eyes of government and corporations to whistleblowing to resistance to tyranny (which was Tor’s original goal when developed by the Naval Research Laboratory and DARPA). It’s not just a compromise of liberty to crack down the network itself, but also quixotic. Just as the NSA’s mass surveillance web has produced very little actionable intelligence by its own account, compromising the technological privacy of the entire law-abiding populace will be much less effective than targeted compromising of human factors. The operators of Silk Road 1.0 and 2.0 are likely stupider than their successors, but no human will ever be as secure as encryption. You can peel away all the technological layers of the onion one by one, or you can quietly follow criminals straight to the core.
