A note to Dutch innkeepers: If you are going to host a convention of lock pickers, and you promise them free Wi-Fi, it is probably a futile gesture to then require paid access with a password. I learned this one evening a few years ago in the Stay-Okay Hostel in Sneek (pronounced like the serpent), a midsized city in the north of the Netherlands. When I asked a conventioneer if Wi-Fi was complimentary, he said there had been some confusion with the hostel. But not to worry, he said: Someone had clandestinely added an access point. I logged on.
In fairness, the conference, known as LockCon, hosted by TOOOL (The Open Organization of Lockpickers, which demurely describes itself as a “growing group of enthusiasts interested in locks, keys and ways of opening locks without keys”) was a far tamer affair than I had expected, given that my visit had been foregrounded with viewings of, for example, a YouTube video showing TOOOL co-founder and president Barry (“the Key”) Wels—as with hackers, a nickname is often de rigueur for lock pickers—opening a standard hotel door, from the outside, using a bent metal bar.
TOOOL, perhaps not surprisingly given that it spends its time figuring out how to open the world’s locks, is sensitive about its portrayal, and LockCon itself is “invitation only.” As Wels had told me, “we spend a lot of time trying to keep the bad guys—or guys with bad intentions—out.” Those who had gathered were a diverse and almost disappointingly legitimate lot, ranging from German pilots to Spanish locksmiths to a British distributed systems architect working in Iceland, not to mention the crew I had traveled with from Amsterdam in a borrowed RV driven by Wels: Deviant Ollam, Datagram, Scorche (and his girlfriend), and Babak Javadi, all members of the American branch of TOOOL and all employed, in one way or another, in the security business. And while LockCon had a whiff of Stieg Larsson—the hacker speak (e.g., “epic fail”) and T-shirts (“Masters of Penetration”), the Northern European location and demographic tilt—its sense of mischief was largely sealed within the confines of the hostel’s conference rooms where, during the day, attendees sat through intensely technical presentations, and by night, fueled by healthy glasses of the hostel’s all-inclusive lagers, engaged in competitive lock-picking trials.
There is an inevitable lure to picking a lock. “A lock is psychological threshold,” writes Gaston Bachelard. The physicist Richard Feynman, himself possessed of what he termed the “puzzle drive” and a notorious lock picker, described it as: “One guy tries to make something to keep another guy out; there must be a way to beat it!” I have a firm memory of clicking open the lock on the bathroom door in my childhood home with a bobby-pin; that the lock is what is called in the business a “privacy lock,” designed not at all for security but merely to prevent unintentional intrusions, did not diminish my ardor in that moment.
Everyone at LockCon seemed to have their own seminal moment. “My first recollection was standing at the gumball machine,” Wels said. “I remember thinking as a child, I know that’s not a difficult lock. I know I’m not skilled enough to open that now, but I know this is not a difficult lock.” Wels did not want to steal the gumballs; rather, he was intrigued by the idea that “there’s something you don’t know yet.” His “hacker spirit” migrated quite naturally to computers—computer hacking, with its “backdoors” and “key spaces,” is nothing if not digital lock picking. So it was with an historical inevitability that Wels would, at a hacker conference in the early 1990s, do an onstage demonstration of lock picking. “Now there’s not a serious security conference that doesn’t have a locksmith village,” notes Wels. Whereas it had taken him several years of effort to acquire his expertise, tracking down as a youth quasi-samizdat lock picking guides like Eddie the Wire’s Complete Guide to Lockpicking, published by the legendary Loompanics, Wels says “the things that took me three years to figure out people now learn in 15 minutes at the lock-pick village.”
I had had my first exposure to real lock picking at one of these villages a month earlier, at the Maker Faire in New York City. When I arrived at the TOOOL tent there, Javadi, shaved-headed and intense, and Deviant Ollam, who faintly resembles a more svelte version of the actor Kevin James, were addressing a rapt crowd.* Loose locks and tools—half-diamonds, Bogotá rakes, Gonzo hooks—were scattered around a table. The first thing to note here is the plural: Contrary to Hollywood depiction, locks, in most cases, cannot be opened with a single tool. Rather, one needs a pick and a tension wrench, or as Javidi described it, a “tension tool.” The word wrench, he suggested, compels people to use too much force. “How much pressure do you need to press the key on a modern laptop keyboard?” Javadi asked the crowd. “You want to use about half that.” Afterward, a boy looked longingly at the pick set I had bought, and I saw the father’s brief reckoning of cost versus son’s happiness. The latter won out.
Picking a basic, modern pin-tumbler lock, the kind most of us encounter in regular life, is simple to understand, but can be achingly difficult to master. When I met Dev, as Deviant Ollam is often called, a few weeks later at a Chinese restaurant in Princeton, N.J., one of the first things he asked, after greeting the server in Mandarin, was that I lay my keys on the table. “This is a Kwikset,” he said, looking at the first. “The head of the key will tell you a lot about the manufacturer.” “That looks like a Schlage there,” he said, identifying my front door key. His eyes narrowed. “There’s not a lot of variation here—looks like you have a 2, 3, 3. I could rake that very effectively.” One of the curious byproducts of spending time with Ollam was that the more we talked about security, the less safe I felt. I began to see the world as a set of glaring weaknesses and loopholes; the architectural standardization brought on by ADA requirements, he mentioned, which tend to put things like door handles (easier to manipulate than knobs) in rote places, were a boon for unauthorized entry. Or, to take the subject of one of his most popular talks at “cons,” the best way to avoid having one’s checked baggage pilfered is to pack firearms, thus demanding the flyer not use a notoriously unreliable TSA-approved baggage lock.
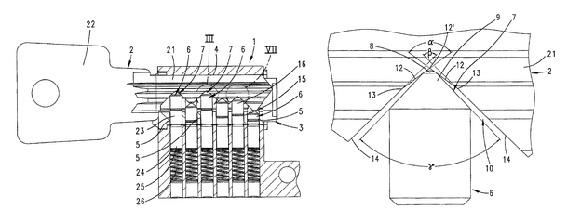
Image courtesy of USPTO
But keys say a lot about locks. Even in everyday use, the lock is a kind of puzzle, as Peter Field, research director at the lock maker Medeco, told me, “and the key is the solution.” If you were to take your keys out now, chances are you would have a key to a pin-tumbler lock. You will see the key “head” (the part that one grips), the key “shoulder” (just below the head, naturally), then a “collar” (that extension that stops the key from going in further). You will then see, along the length of the key, a series of slopes and valleys (reminding me of the jagged, scrolling landscape from the old video game Defender). These are known as “bitting cuts,” and the progression of these cuts is referred to as the “bitting code.” A “1” cut is quite shallow; a “9” is very deep. For mechanical reasons, the bit depths cannot vary too widely from one to another; a “1” cannot follow a “9.” When the key is inserted, these cuts sweep across a series of segmented pins that keep the cylinder from turning. The correct key will come to rest in such a position that the pins have been pushed to the “shear line,” that small gap between the inner and outer cylinders, which allows the inner cylinder to turn and the lock to open. To “rake” the lock is to take a tool, thin and curvy at its tip, and rapidly “scrub” in and out of the lock. As Ollam notes in his book Practical Lock Picking, this can be brutally effective, “with the lock popping open so suddenly as to take a person by surprise.”
“Small imperfections in the way a lock is machined go a long way toward making picking possible,” Ollam told me. The edge of a pin may be chipped, or the pin chambers out of alignment. Feynman describes the process: “Now, if you push a little wire gadget—maybe a paper clip with a slight bump at the end—and jiggle it back and forth in the lock, you’ll eventually push that one pin that’s doing the most holding, up to the right height. The lock gives, just a little bit, so the first pin stays up—it’s caught on the edge. Now most of the load is held by another pin, and you repeat the same random process for a few more minutes, until all the pins are pushed up.” The process is called “setting the pins”—with raking, a number of pins are often set at once. “When you feel that first click,” Ollam said, “it can be profound.”
None of this is easy, however, as I learned at LockCon, sitting in the hostel bar with John Naughton, an English civil servant and lock-picking enthusiast. As a languid, jazzy cover of “Billie Jean” played in the background, I struggled over a variety of European locks (which, by LockCon consensus, are generally superior to American locks—apparently they have tighter “keyways”). “It took me hours to get my first lock,” Naughton said, counseling me through rookie mistakes like “overlifting,” or pushing the pin stack past the shear line, meaning, basically, one has to start over. Our efforts soon attracted a jovial group of local men, who began plying us with metworst (“special Dutch meat”) as they watched us closely, only adding to my howling anxiety. “Don’t worry,” said Naughton, “it always draws an audience.” We were joined by Jaakko Fagerlund, a taciturn Finn with pale skin and strikingly black hair. Naughton told me that Fagerlund had found a way to exploit a manufacturing deficiency of a different sort: In the original model of the Abus Granit lock, the manufacturers had stamped the bitting code inside the lock. Fagerlund created a tool that, with a bit of blue tack applied to the end, could “read” the code—allowing him to make a key.
Locks tell stories. “Your nose can tell whether a lock has been lubricated recently,” advises The MIT Guide to Lock Picking. “You want to project your senses onto the lock to receive a full picture of how it is responding to your manipulations.” One classic tactic is “impressioning,” or making a duplicate key based on information extracted from the lock. Naughton and I soon headed upstairs, where the Dutch Open impressioning championships were about to begin. A dozen or so people were seated at small tables, each with a lock clamped in a vise, surrounded by myriad files and workbench magnifiers. When a TOOOL member counted three, the room erupted with the high-pitched screech of files on metal. As Naughton explained it to me, the trick was to insert a key “blank,” (the sort one gets at a hardware store when having a key copied), turn it with force, then look for tiny but telltale indentations. “Every time you see a mark, you file it down a step,” Naughton said. “When you no longer see a mark, it means another one’s binding or that one’s done.” The idea, Naughton said, is that “you end up with a key that works in the end—it’s easier to get in next time.” My eyes were drawn to a stocky Dutchman with a bald head and a kilt. He would crank the key in the lock tremendously, in rapid succession, whip it out, rotate it and peer intently at it under a magnifier, then take several upstrokes with a file—notching roughly one “depth” with each stroke—then repeat the process. This, it turned out, was Jos Weyers, possessor of the impressioning speed record. A minute later, he shouted “open” and raised his hands.
The next night, the lock-picking championships were held in a similar setting, though this time the noise resembled a thousand mechanical crickets, as participants delicately probed or violently scrubbed the locks before them. Competition of any sort tends to fall along familiar narrative lines. There was, for example, the intimidating presence of the Germans, who tend to dominate locksport, and as the rounds progressed, it was not uncommon to hear a winning cry of “offen”—often, disconcertingly, a half dozen seconds after the starter’s command. The underdog, for me and the fellow Americans, after they themselves had been eliminated, was Naughton, who cleared several rounds, red and sweating at the end of each. But he too soon fell. The eventual winner was Arthur Meister, a big, gregarious German—a member of the Hamburg branch of the locksport group SSDeV—with leather pants and a ferocious spiked mullet.
And while it initially seemed strange, these men (and a few women) hunched over locks on a Saturday night, I soon found myself carried along by the proceedings, and it began to dawn on me that here were the descendants of the legendary 19th-century American lock pick Alfred C. Hobbs, the man who’d shown up Britain’s master locksmiths with his suitcase of picking tools. But these modern enthusiasts were working not for rival manufacturers but for the sheer spirit of the thing. “For me it has to do with the quest for the perfect lock,” Wels told me. “I always want to know what the state of the art is—what comes out if clever people really put their effort to it and make the best they can.”
He demonstrated the exacting level of this interest in an afternoon talk on ARX pins, a pick-resistant technology found in the latest generation of high-security Medeco locks. With taxonomic rigor, Wels ran through myriad (and seemingly endless) permutations of the small metal bits, and puzzled out loud, in a kind of exercise in group epistemology, the meaning of their variations. “Could this be a limitation of the milling process?” someone asked from the audience. “No,” said Wels. “These people know what they’re doing. This is not a limitation.” After cataloging some 30 pin variations, Wels concluded: “I don’t know the classification, but it would be fun to figure it out,” he said. “If you go to one island and see a monkey with one stripe on his back, and go to another island and see a monkey with three stripes on his back, there’s probably also an island with monkeys with two stripes.” Laughter from the audience. “This is how I look at it.”
At one level, LockCon was an exercise in the almost ironically outsized bravado of geek one-upmanship (stickers for the “Masters of Penetration” group featured a mudflap girl curled around a pick). At one point, Datagram, who does “lock forensics” in addition to computer security work, presented a lock he had opened to a small circle of people. Impressed, they pressed for the secret. “BDG,” he said. This drew quizzical looks. “Be Datagram.”
But at another level, the members of TOOOL (and other groups, like SSDeV) are exposing real flaws in the products of multinational corporations, products that consumers assume, with a certain amount of faith, cannot be easily compromised. And TOOOL, to its credit, takes on this responsibility with a certain gravitas. “What we did with TOOOL, from the very beginning, was warn manufacturers that if we discovered a problem, we’ll always give them at least six months,” Wels said.
This philosophy echoes an old debate in the security world. Alfred Hobbs, in his Rudimentary Treatise on the Construction of Locks, had noted: “A commercial, and in some respects a social, doubt has been started within the last year or two, whether or not it is right to discuss so openly the security or insecurity of locks. Many well-meaning persons suppose that the discussion respecting the means for baffling the supposed safety of locks offers a premium for dishonesty, by shewing others how to be dishonest.” Hobbs certainly didn’t buy this argument, but this ethos has long held sway among locksmiths, a trade born of closed medieval guilds. As Ed Roskelly, a New Jersey locksmith, told me at LockCon, “in the 1970s, it was a very closed profession. Unless you were related you weren’t getting in.” Books like The Art of Manipulation, an out-of-print guide to opening safes, came cloaked with warnings: “We also suggest after you become proficient in the art of manipulation to destroy this book completely, so as to protect yourself and our craft.” As Matt Blaze notes, this approach has not rested comfortably with the open-source world of “white hat” hackers, which derides “security through obscurity.” As one source describes it, this is software vendors’ “favorite way of coping with security holes—namely, ignoring them, documenting neither any known holes nor the underlying security algorithms, trusting that nobody will find out about them and that people who do find out about them won’t exploit them.”
A few days before LockCon, Ollam and Javadi had visited a large security convention in Essen, Germany. There, they had come across a German company selling a new lock, promoted via its website as the “the safest locking system in the world.” Their interest naturally piqued, they tried, unsuccessfully, to pick it. They then, with admirable tact, persuaded the company to let them borrow the prototype and bring it to LockCon. The manufacturers, much as Bramah had more than a century before in his shop on Piccadilly, granted the request with a kind of casually bemused interest. In Sneek, after managing to crack it themselves, Ollam and Javadi began passing it around. They wrote the opening times on a piece of a paper (awarding the winner, as Ollam said, a pair of “high-end Korean handcuffs from my private stock”). They locked the list inside of the lock’s cylinder, and sent the whole thing back to the manufacturer. Upon receiving the package, the manufacturers (who Ollam did not want named, as per the ethics of disclosure) were, as Ollam later described it, incredulous and more than a bit fascinated, and in the midst of discussions with the lock pickers on how to improve their product.
This was Hobbs 2.0. It was the old cloistered lock world meeting the open-source ethos of Linus’ Law (after Linus Torvalds, the Finnish hacker and creator of Linux): “Given enough eyeballs, all bugs are shallow.” This is not to say this relationship is entirely comfortable. When Peter Field of Medeco, a company that has been the focus of well-publicized attacks (and an entire book, Open in Thirty Seconds), gave a four-plus-hour presentation on lock design—he began with the proviso, “I talk about how they’re made, I don’t talk about how to compromise them”—and ended by quoting Thomas Friedman’s The World is Flat: “It’s not only the software writers and computer geeks who get empowered to collaborate in a flat world. It’s also al-Qaida and other terrorist networks. The playing field is not being leveled only in ways that draw in and superempower a whole new group of innovators. It’s being leveled in a way that draws in and superempowers a whole new group of angry, frustrated, and humiliated men and women.” There was an uncomfortable silence, and some awkward seat-shifting, as Field closed the book; whether intended or not, it seemed to come off as an admonition.
Update, March 26, 2013: This article originally included a reference to Deviant Ollam’s real name. His name was removed because of a pre-existing agreement between the author and Deviant Ollam to use only his pseudonym in this story.
Correction, March 12, 2013: On subsequent references to Babak Javadi, this article originally misidentified him twice as “Savadi.” (Return to the corrected sentence.)
